-
Notifications
You must be signed in to change notification settings - Fork 45
Azure Access Control Service
There are a couple of gotchas regarding Azure ACS's relying party (RP) realm configuration that could leave you spending your valuable development time troubleshooting validation errors in the WSFed sign-in authentication callback.
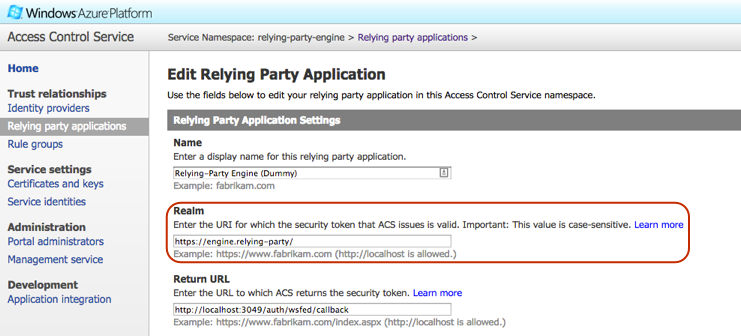
Under certain circumstances, Azure ACS will automatically add trailing slashes to the RP realm URI. When ACS modifies the realm URI, the UI properly reflects the change but it fails to notify the administrator that the change took place. You can read a bit more about this particular issue here. It's not necessarily an issue with the gem or with ACS (well, maybe with ACS), but it could cause some headaches and validation errors. If your ACS RP configuration contains a trailing slash, ensure that your omniauth-wsfed configuration includes it as well.
- ACS automatically adds a trailing slash to all realm URIs containing root domain information only.
- Example:
https://your-organization.comwill automatically be converted tohttps://your-organization.com/.
- Example:
- ACS refrains from inserting trailing slashes for any realm URI containing subfolder detail in addition to the root
domain. Trailing slashes are allowed here if entered manually, but they are not automatically added by ACS.
- Example 1:
https://your-organization.com/relying-party-nameis accepted without a trailing slash auto-insert. - Example 2:
https://your-organization.com/another-relying-party/is accepted when inserted manually.
- Example 1:
Typically, ACS forces an exact match between its RP realm URI configuration and the realm URI configuration in your omniauth-wsfed implementation. There is one unique circumstance where this is not exactly the case. If you configure ACS's realm URI with root domain information only, your omniauth-wsfed realm URI configuration may contain additional subfolder information as long as it contains the same root domain detail.
- Example: ACS will issue a valid AuthN token for your omniauth-wsfed callback if,
- ACS's realm is configured as
https://your-organization.com/, and - omniauth-wsfed's realm is configured as
https://your-organization/subfolder.
- ACS's realm is configured as
Azure ACS supports this behavior to allow RPs multiple reply-to endpionts (something that omniauth-wsfed doesn't support). You can read about this in more detail in the official ACS documentation.