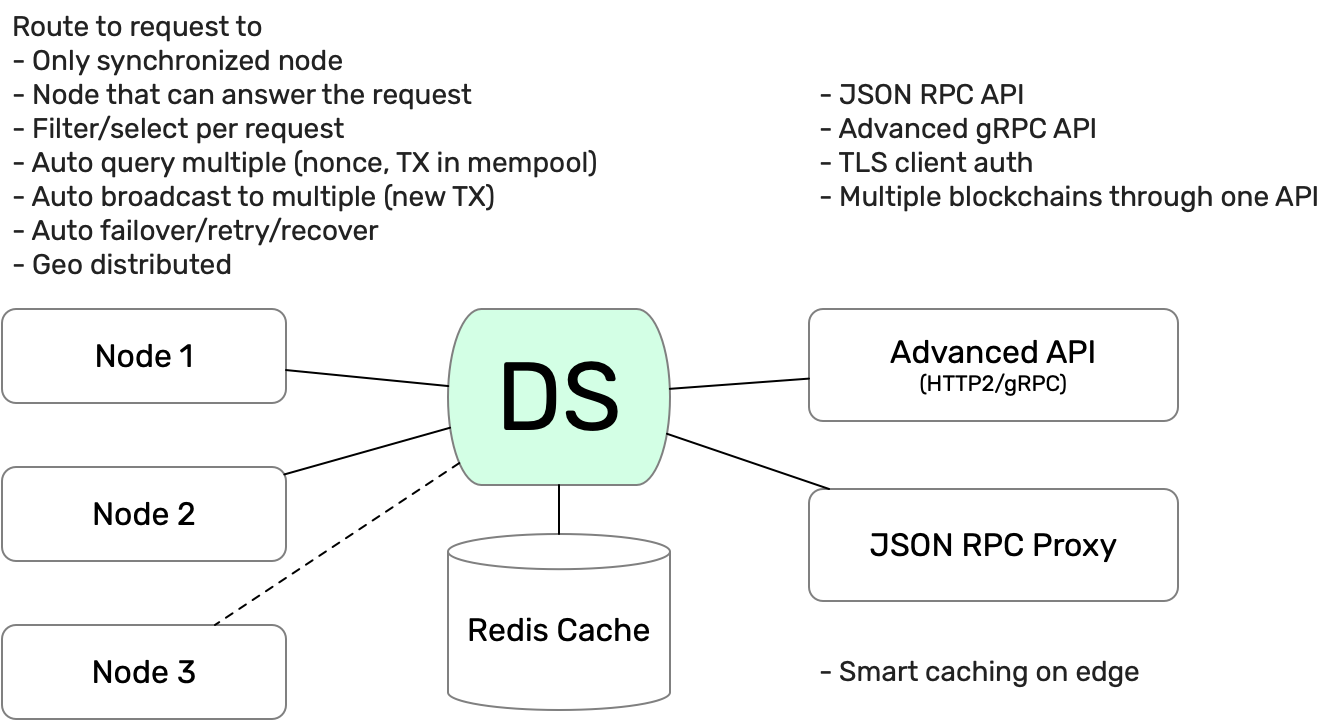
Dshackle is a Fault Tolerant Load Balancer for Blockchain API used at DRPC
Is is a fork of the EmeraldPay’s dshackle, adapted to work as a provider side adapter for the DRPC network. This project is specifically designed to integrate providers into the DRPC network, which is distinguished by its focus on low latency and high availability. Our service facilitates providers in easily connecting to the DRPC, enabling them to be part of a network that prioritizes robust, consistent, and responsive operations. Joining this network through our adapted service allows providers to contribute towards creating a highly available and resilient decentralized system.
The goal of the Dshackle is to provide a stable routing to multiple nodes, and ensure that each request is executed on an appropriate provider. It considers nodes locations, state, current height, RPC methods it can provide and other characteristics.
It tries to recover from connection errors, faulty nodes, invalid responses, etc. If upstream lags behind others, lost peers below required, started to resync or went down, then Dshackle temporarily excludes it from requests and returns it when the upstream problem is fixed.
The upstreams may be blockchain nodes such as Bitcoind, Geth, Parity, or public providers like DRPC. It automatically verifies their availability and the current status of the network, executes commands making sure that the response is consistent and/or data successfully broadcast to the network.
Provides:
-
Standard Bitcoin and Ethereum JSON RPC API over HTTP and WebSocket
-
Enhanced gRPC-based API, with upstream selection, async execution, etc
-
Secure TLS with optional client authentication
-
Blockchain-aware edge caching, in memory and Redis
-
Routing based on data availability (peers, height, sync status)
-
Data consistency, it always gives a most actual state
-
Automatic failover and retry
-
Separate public blockchain nodes from your internal servers
List of supported chains here. Feel free to contribute new chains.
Create file dshackle.yaml with the following content:
version: v1
port: 2449
tls:
enabled: false
proxy:
host: 0.0.0.0
port: 8545
routes:
- id: eth
blockchain: ethereum
- id: btc
blockchain: bitcoin
cluster:
upstreams:
- id: drpc-eth
chain: ethereum
connection:
generic:
rpc:
url: "https://lb.drpc.org/ogrpc?network=ethereum&dkey=${DRPC_KEY}"
ws:
url: "wss://lb.drpc.org/ogws?network=ethereum&dkey=${DRPC_KEY}"
- id: solana
chain: solana
connection:
generic:
rpc:
url: "https://localhost:8899"
ws:
url: "wss://localhost:8900"
- id: bitcoin-main
chain: bitcoin
connection:
bitcoin:
rpc:
url: "http://localhost:8332"
basic-auth:
username: bitcoin
password: mypasswordWhich sets the following:
-
gRPC access through 0.0.0.0:2449
-
TLS security is disabled (please don’t use in production!)
-
compression is disabled for gRPC server (enabled by default)
-
-
JSON RPC access through 0.0.0.0:8545 (both HTTP and WebsScket)
-
proxy requests to Ethereum and Bitcoin upstreams
-
request path for Ethereum Mainnet is
/ethand/btcfor bitcoin -
i.e. call Ethereum Mainnet by
POST http://127.0.0.0:8545/ethwith JSON RPC payload
-
-
three upstreams - ethereum, solana and bitcoin
-
for Ethereum Mainnet it connects using JSON RPC and WebSocket connections,
-
for Bitcoin Mainnet only JSON RPC is used
-
${DRPC_KEY}will be provided through environment variable
Please note that you can configure many upstreams for a single blockchains. If there is more than one upstream, then Dshackle routes requests to them as Round Robin. If one of them becomes unavailable, Dshackle continues to use only active nodes.
I.e., you can set up a node in the local network, plus Infura with role: fallback.
If anything happened to your local node, you still have access to a consistent state of the Ethereum blockchain via Infura.
Official Docker image you can find at: drpcorg/dshackle
export DRPC_KEY=...docker run -p 2449:2449 -p 8545:8545 -v $(pwd):/etc/dshackle -e "DRPC_KEY=$INFURA_USER" emeraldpay/dshackle:0.12Now it listens on port 2449 at the localhost and can be connected from any gRPC compatible client. Tools such as gRPCurl can use protobuf definitions from proto reflection and connect to it
Alternatively you can connect to port 8545 with traditional JSON RPC requests
For detailed documentation see docs/ directory.
|
Warning
|
The code in master branch is considered a development version, which may lack proper testing and should not be used in production.
|
There is a short guide "How to write tests in dshackle"
-
First of all, all new tests must be written in Kotlin. Groovy tests are fixed only if necessary.
-
To create mocks we use
org.mockito.kotlin.mock(instead ofMockitoclass) and all extensions from that package, so that we can write our test code in kotlin-style. -
There are 2 main assertion libs in kotlin: the basic one
org.junit.jupiter.api.Assertionsand the more advancedorg.assertj.core.api.Assertions.-
junit assertion lib is super simple - there are a lot of assert functions that just compare inputs
-
assertj lib is a much more advanced lib that provides a rich set of assertion methods that read like natural language. For example, you can write assertions like
assertThat(result).isEqualTo(expected)orassertThat(list).containsExactly(1, 2, 3). This makes your tests more self-explanatory and easier to understand. Also, you can easily compare objects with ignoring some fields that sometimes can be really useful. And many other features.
-
-
To sum up, for assertions let’s use
assertjlib. -
To test the reactive code we use
StepVerifierfrom the reactor package. Just callcreatemethod and pass yourFluxorMonoand add necessary assert methods which start with theexpectprefix. Also, if your reactive pipeline is dependent on periodic operations you can usewithVirtualTimemethod, with which you no longer need to work with real time.
Join our Discord
Copyright 2021 EmeraldPay, Inc
Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at
Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License.