-
Notifications
You must be signed in to change notification settings - Fork 0
Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
- Loading branch information
1 parent
1ee1b4e
commit d707d9c
Showing
5 changed files
with
117 additions
and
32 deletions.
There are no files selected for viewing
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -0,0 +1,12 @@ | ||
| [[source]] | ||
| name = "pypi" | ||
| url = "https://pypi.org/simple" | ||
| verify_ssl = true | ||
|
|
||
| [dev-packages] | ||
|
|
||
| [packages] | ||
| scapy = "*" | ||
|
|
||
| [requires] | ||
| python_version = "3.7" |
Some generated files are not rendered by default. Learn more about how customized files appear on GitHub.
Oops, something went wrong.
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| Original file line number | Diff line number | Diff line change |
|---|---|---|
| @@ -1,9 +1,35 @@ | ||
| # PI3Dos attack | ||
| # PI3DoS attack | ||
|
|
||
| ## Description | ||
|
|
||
| This attack destroys everything on it's way. | ||
|
|
||
| PI3Dos attack stands for | ||
| - **PI** - | ||
| PI3DoS attack stands for | ||
| - **PI** - TCP packet configuration is based on the first 100_000 numbers of the [Pi](https://en.wikipedia.org/wiki/Pi) | ||
| - **3** - TCP's 3-way handshake | ||
| - **Dos** - Denial Of Service | ||
| - **DoS** - Denial Of Service | ||
|
|
||
| This DoS attack is an implementation of the **SYN Flood Attack**. | ||
| Here is a diagram of how it works 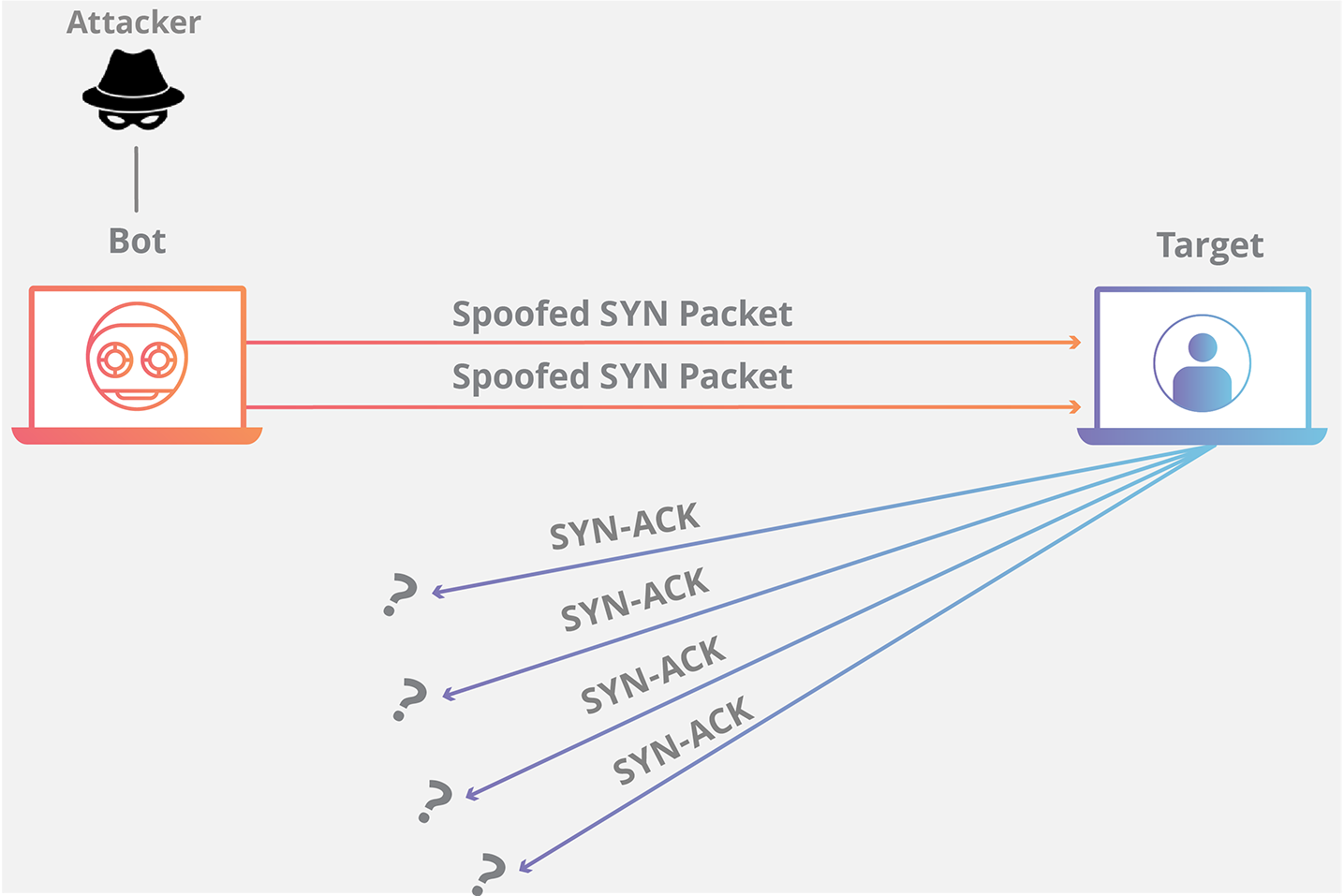 | ||
| For more info visit [syn flood ddos attack](https://www.cloudflare.com/learning/ddos/syn-flood-ddos-attack/) | ||
| First 100_000 numbers of the PI are received from the [PI.txt file](https://github.com/artemgurzhii/Pi3DOS-attack/blob/master/PI.txt) | ||
|
|
||
| ## Prerequisites | ||
|
|
||
| You will need the following things properly installed on your computer. | ||
|
|
||
| * [Git](https://git-scm.com/) | ||
| * [Python](https://www.python.org/) | ||
| * [Pipenv](https://github.com/pypa/pipenv#installation) | ||
|
|
||
| ## Installation | ||
|
|
||
| * `git clone https://github.com/artemgurzhii/Pi3DOS-attack` this repository | ||
| * `cd Pi3DOS-attack` | ||
| * `pipenv install` | ||
| * `sudo python3 main.py` | ||
|
|
||
| ## Acknowledgments | ||
|
|
||
| [Artiikk](https://github.com/Artiikk) | ||
| [sawezx](https://github.com/sawezx) |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters